Best Practices for Virtualization on the Windows Platform

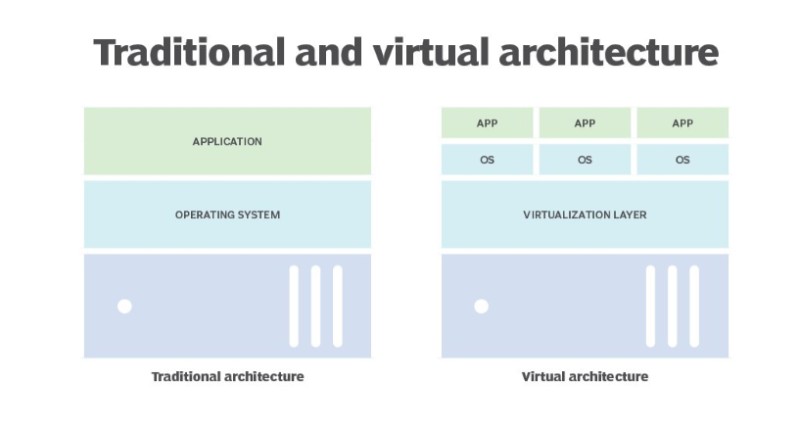
While managing virtual servers offers advantages over physical servers, it introduces new challenges. In the past, when each workload had its dedicated physical server, administration was straightforward. Any issues were addressed at the specific server, and all resources for a workload resided on that server.
However, with the shift to virtualization, users can request VMs through a self-service portal, resulting in quick deployment of new workloads. This change necessitates shared hardware resources and collaborative management, transforming the IT landscape.
Utilize Self-Service Management to Mitigate VM Sprawl
The ease of creating virtual machines (VMs) often leads to the challenge of VM sprawl, where VMs proliferate without clear purposes. Paradoxically, implementing self-service VM management can be a proactive solution to address this issue. Allowing users to request and manage their own VMs empowers them to take responsibility for their resources.

By deploying VMs with a lease time, users are prompted to reassess the necessity of the VMs when the lease expires. Additionally, integrating a budgetary charge for VM usage incentivizes users to tidy up unused resources. In VMware environments, systems like vRealize Automation provide a self-service catalog for users to request services and autonomously manage their VMs.
Optimizing VM Sizing with Templates
When generating virtual machines (VMs), the inclination is often to allocate more resources than necessary, thinking it will enhance performance. However, this commonly leads to resource wastage, especially when multiplied across a large environment.
An uncomplicated yet effective solution, which requires no additional software investment, is to implement templates of predefined sizes – essentially, a menu offering various VM configurations. This approach prevents administrators from unintentionally creating oversized VMs.
Virtualization on the Windows Platform
Incorporate subtle psychological strategies by arranging the menu with the preferred VM type listed first, such as two CPUs and 4 GB RAM. This primes users to opt for the second smallest or medium-sized option, aligning with the desired configuration. This psychological tactic mirrors the effectiveness seen in self-service product menus.
Leverage Monitoring Tools for Performance Oversight
Even with a well-organized system, administrators cannot afford to be complacent. Vigilance is crucial to identify potentially underutilized or oversized VMs that may no longer be in use. Tools like vRealize Operations Manager or Microsoft System Center prove invaluable in this regard, offering insights into system performance and deployment efficiency.
Given the shared hardware resources in virtualized environments, understanding resource utilization becomes paramount. Standard tools bundled with hypervisor licenses, such as vCenter for VMware, enable administrators to scrutinize performance in smaller-scale deployments.
As the environment expands, encompassing multiple vCenter servers across various data centers, additional software becomes imperative. Alternative solutions from vendors like SolarWinds, Datadog, and ManageEngine offer comparable functionality for VMware or other virtualization environments.
Safeguard VMs with Robust Permissions Management
Transitioning from a physical to a virtual environment often involves delegating management responsibilities to others. Establishing a well-thought-out plan for delegating administration to the right users is essential. Most hypervisors, such as VMware vCenter, offer a permissions model that allows configuring a hierarchy reflecting the areas of the environment requiring delegated administration with precise permissions.

Virtualization on the Windows Platform
Utilizing groups, akin to those in Active Directory, proves to be the most effective strategy. Groups facilitate easy assignment and, more importantly, seamless revocation of permissions by adding or removing users from the group. Admins can efficiently audit permissions by reviewing group memberships.
Enhance Security with VPN and Multifactor Authentication for Remote Access
The shift from a physical to a virtual environment alters the attack surface, posing different security challenges. Unlike physical servers, where breaching one server may not grant access to others, centralized VM management in a virtual environment exposes the entire system to risk when the platform is compromised.
In today’s remote-working landscape, where administrators manage environments from home, establishing a robust remote access method is paramount. Traditional approaches, like using remote desktop servers to access the data center and subsequently manage the infrastructure, have proven to be less secure. A more secure alternative is to implement a VPN connection coupled with multifactor authentication.
Opt for a Dedicated Backup and Restore Platform for VMs
In a physical environment, each server typically has its backup created with an agent running within the operating system. While this approach is feasible in a virtualized setting, it often leads to performance issues due to the substantial data that needs to be retrieved from the hypervisor.
Adopting a VM-centric backup strategy involves collecting and storing only the VM’s metadata, OS, and application information. This data is often consolidated into a single file containing all the necessary information for restoring that VM on any physical server. Accessing individual files within the backup set can be challenging, so it’s crucial to select a VM backup platform that facilitates individual file restores.