Top 10 Security Improvements in Windows Server 2019
Top 10 Security Improvements in Windows Server 2019
The latest version of Windows Server introduces significant security upgrades compared to Windows Server 2016, including tools for monitoring ransomware and other malware, as well as tracking extended perimeter exploitation attacks.
Windows Server 2019 integrates with Windows 10 1809 by adding crucial security enhancements extremely useful for Server administrators. This release, available with the Desktop Experience option, is part of the Long-Term Servicing Branch (LTSB) for the Windows Server series. For those uncomfortable with operating servers without a Graphical User Interface (GUI), this is the preferred version for serving as the foundation for Remote Desktop Servers and Exchange 2019.
Users familiar with Windows Server 2016 will find Windows Server 2019 quite similar. However, several security improvements make Windows Server 2019 a preferred choice. Here are the most significant enhancements for security features or administrative functions that simplify security-related tasks.
1. In-place Upgrade Unlike Windows 10, upgrading from Windows Server 2016 to Windows Server 2019 requires a license. In-place upgrade is fully supported for moving from Windows Server 2016 to Windows Server 2019, excluding the Essentials role no longer included in Windows Server 2019.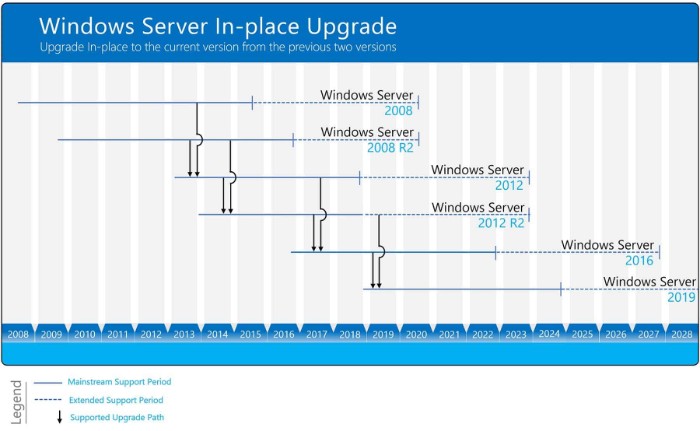
2. Security Bug Fixes Windows Server 2019 and Server with Desktop Experience receive security bug fixes similar to those in Windows Server 2016. However, it does not receive semi-annual feature releases like desktop Windows 10; instead, it gets monthly security bug fixes. Windows Server Core, a GUI-less option, receives updates semi-annually in October. It is recommended to connect Server Core with the new Windows Admin Center for server management.
3. .NET Updates Similar to Windows 10 1809, Windows Server 2019 receives its .NET updates as a separate package that can be installed or uninstalled independently of the Windows operating system. This flexibility allows users to install .NET Framework updates selectively to ensure compatibility with Exchange 2019 or other enterprise applications.
4. Advanced Threat Protection (ATP) A new additional feature is Advanced Threat Protection (ATP), originally introduced in Windows 10 and now extended to Windows Server. With an added Azure Security Center license, users gain enhanced capabilities to monitor attackers and track extended attack surface actions on the server. Extended attack surface attacks and the use of PowerShell to access the system are monitored and recorded for later analysis.
5. Windows Defender ATP Exploit Guard For those who have deployed Windows 10, the security enhancements provided by Windows Defender ATP are likely familiar. Windows Server 2019 adds intrusion prevention capabilities to the server. Windows Defender Exploit Guard’s task is to “lock” devices to resist a range of attack vector behaviors.
- Attack Surface Reduction (ASR) includes control actions to prevent malicious software from infiltrating the machine, blocking suspicious malicious files (especially manually crafted Office files), scripts, extended exploitation, ransomware, and threats through email.
- Network Protection adds endpoint protection, preventing web-based threats by blocking any data transmission process from the device to untrusted servers or IP addresses through Windows Defender SmartScreen.
- Ransomware Protection is provided by Access Folder Access, a tool protecting sensitive data from ransomware by blocking unauthorized processes from accessing user-protected folders. This can be customized to add folders that users want to protect.
- Exploit Protection is a set of actions that minimize vulnerability exploitation, configurable to protect your system and applications. This replaces the Enhanced Mitigation Experience Toolkit (EMET), which is no longer in use.
- Code Integrity policy, introduced in Windows Server 2016, was challenging to deploy. Therefore, Windows Defender Application Control now includes default Code Integrity, allowing applications like SQL Server to block known executable files.
6. Security Improvements in Software-defined Networking In Windows Server 2019, Software-defined Networking has been enhanced to create a firewall log with the same classification format as Azure Network Watcher. Hyper-V servers generate records that can be analyzed with various log file format support tools. Windows Server 2019 integrates the network security lockdown capabilities of Windows Server 2016 by automatically applying Access Control Lists (ACLs) to virtual machines (VMs) connected to virtual subnets and other structures. Windows Server 2019 allows you to restrict access by adding ACLs to the corresponding subnet.
7. Enhancements for Shielded VM When setting up secure branch offices using shielded VMs, you can ensure uninterrupted access to the Host Guardian Service by establishing a backup Host Guardian Service and an offline mode. This ensures you can establish a second URL group as a backup for Hyper-V servers to use if the primary Host Guardian Service is inaccessible.
Windows Server 2019 also provides additional support for VMConnect Enhanced Session mode and PowerShell Direct to facilitate troubleshooting for protected virtual machines. These features are automatically activated when a protected virtual machine is placed on a Hyper-V server running Windows Server 2019 or Windows Server version 1803 or later (Windows Server 2019 with Desktop Experience or Windows Server Core).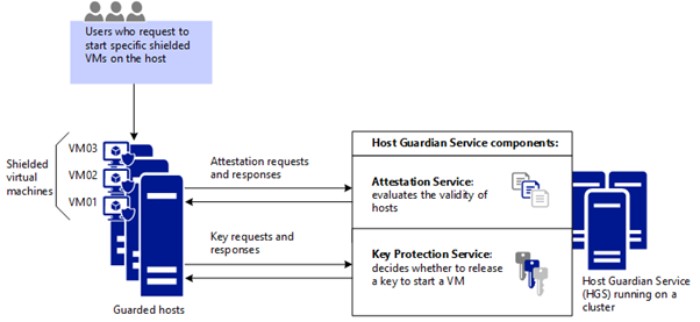
8. Linux Support In Azure, Linux is widely used. Windows Server 2019 fully supports running Ubuntu, Red Hat Enterprise Linux, and SUSE Linux Enterprise Server inside protected virtual machines. Microsoft is developing it as a protective tool for Linux, not as a competitive opponent. Recently, Microsoft joined the Open Invention Network (OIN), a community dedicated to protecting Linux and other open-source software from patent-related risks. By participating in this project, Microsoft allows the Linux community to use 60,000 patents for free without the risk of litigation.
9. Enhanced HTTP/2 Included in Windows Server 2019 are improvements to make websites faster and more secure. HTTP/2 represents a significant improvement over current HTTP technologies. Enhancements include better server-side encoding, reducing automatic connection issues. Deploying these new applications in a user environment is also easier.
HTTP/2 shares a single TCP connection with multiple requests to the same website. During sharing or channel aggregation, only the first request incurs the necessary back-and-forth processes to establish a connection. Subsequent requests immediately send HTTP data for connectionless requests.
Domains designed for HTTP/1.1 are not without benefits. Connection synchronization features are added to minimize sharding (sharding is a process that distributes data records across multiple devices to meet data growth requirements) and are activated on both Edge and HTTP servers. With consolidation, stored subdomains will end sharing a single TCP connection if their certificates match. Without this synchronization setting, websites like 1.bing.com and 2.bing.com will require separate TCP connections.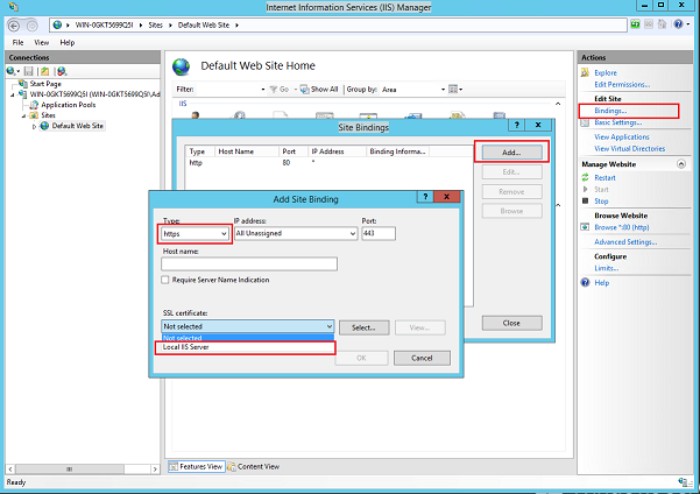
Windows Server 2019 automatically works to address connection errors. HTTP/2 requires at least TLS version 1.2 while listing lower cipher suites. This leads to broken connections. On current servers, until the encryption is fixed, connections will not work smoothly. Some changes in Windows Server 2019 ensure that reconnection will be performed.
As mentioned, these are the steps Microsoft takes in Windows Server 2019 to address the issue:
- Failure modes occur when the default SSL encryption in Windows Server 2016 is inaccurately changed. If any encryption is blocked by HTTP/2 or appears before HTTP/2-enabled encryptions, Firefox and Chrome will terminate the connection (allowed but not recommended by HTTP/2). Chrome displays: ERR_SPDY_INADEQUATE_TRANSPORT_SECURITY, and Firefox displays: NS_ERROR_NET_INADEQUATE_SECURITY.
- Properly arranging SSL encryptions (ensured by default order in Windows) can avoid this issue. In Windows Server 2019, the robust capabilities of the cryptographic negotiation mechanism to rearrange SSL encryptions have been improved. Of course, this list still needs to include HTTP/2-enabled encryptions, but they don’t necessarily have to appear at the beginning of any blacklist.
This reduces the complexity of deploying HTTP/2, allowing customers to easily reap its benefits, including premium encryptions required by HTTP/2.
10. Traffic Control Finally, Windows Server 2019 includes support for congestion control tools New-Reno, Compound TCP, Cubic, and LEDBAT (Cubic is the new default). Cubic is well-suited for bandwidth and high-latency links, while standard TCP performs poorly in these situations.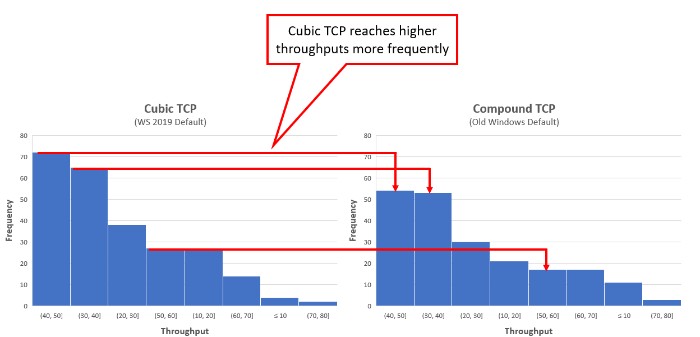
All these changes are added to provide server and web administrators with more options to ensure security, as well as safe storage and distribution of data.


